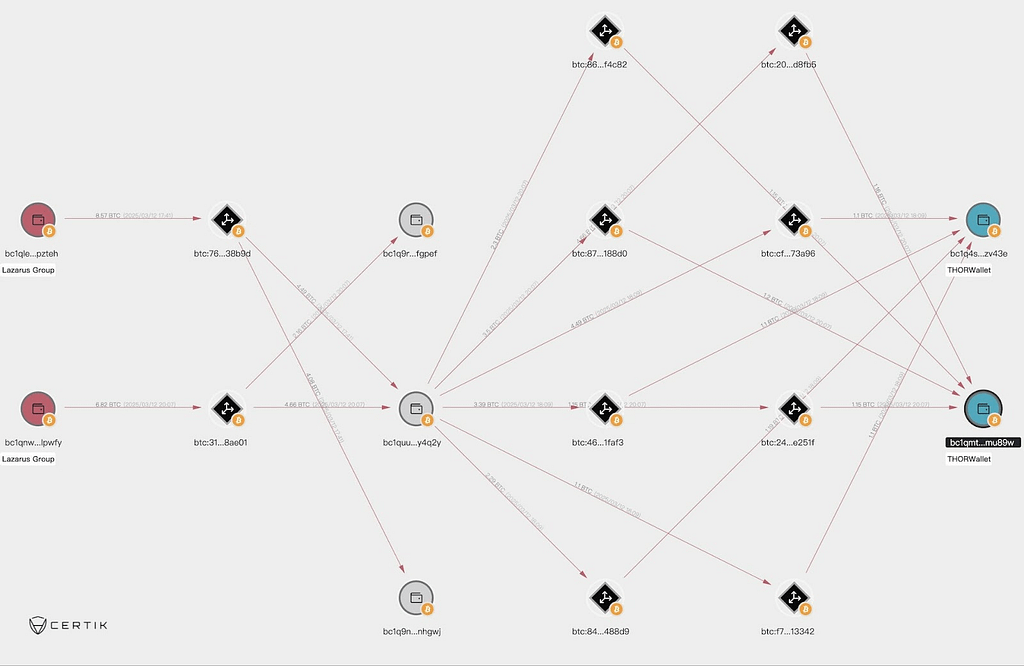
Looks like Lazarus Group is back at it again. The notorious North Korean hacker collective has been laundering Ethereum and unleashing fresh strains of malware targeting crypto developers — and this time, it’s a big one.
On March 13, blockchain security firm CertiK alerted its followers on X (formerly Twitter) that they had discovered a stash of 400 ETH — worth about $750,000 — being funneled through Tornado Cash, a well-known crypto mixer. According to CertiK, these funds are linked to Lazarus Group’s past Bitcoin network exploits.
This isn’t exactly a surprise. Lazarus Group has a track record of high-stakes crypto heists. In fact, they were behind the massive Bybit hack on February 21, which saw $1.4 billion in crypto assets vanish into thin air. Oh, and don’t forget the Phemex breach in January, where they swiped another $29 million. Since then, they’ve been busy laundering those stolen funds.
Lazarus Group’s Crypto Trail of Destruction
Lazarus has a long history of pulling off some of the biggest crypto hacks on record. Remember the Ronin Network breach in 2022? That one cost the network a staggering $600 million. And they’re not slowing down — according to Chainalysis, North Korean hackers looted more than $1.3 billion in cryptocurrency across 47 attacks in 2024 alone. That’s more than double the number of incidents from 2023.
New Malware Targeting Developers
But here’s the real kicker: Lazarus isn’t just after crypto exchanges anymore — they’re now targeting developers. Cybersecurity researchers at Socket uncovered six new malware packages designed to infiltrate developer environments, steal credentials, mine crypto data, and install backdoors.
The malware was spotted in the Node Package Manager (NPM) ecosystem — basically, the go-to library for JavaScript developers. One of the malicious packages, named “BeaverTail,” was cleverly disguised as a legit library through a tactic called typosquatting — where hackers create fake packages with names almost identical to trusted ones, hoping developers will download them by mistake.

And it doesn’t stop there. This malware also goes after crypto wallets — particularly Solana and Exodus — and even targets browser data from Google Chrome, Brave, and Firefox. MacOS users are especially vulnerable, as the malware can sneak into keychain data.
Researchers admitted that pinning these attacks directly on Lazarus is tricky. But the tactics, techniques, and overall playbook? Classic Lazarus.
Lazarus Group seems to be evolving — mixing high-stakes crypto heists with more sophisticated infiltration strategies. If you’re a developer, you might want to double-check those NPM packages before hitting install.

